18+ Money laundering techniques with electronic payment systems information
Home » money laundering idea » 18+ Money laundering techniques with electronic payment systems informationYour Money laundering techniques with electronic payment systems images are ready in this website. Money laundering techniques with electronic payment systems are a topic that is being searched for and liked by netizens now. You can Download the Money laundering techniques with electronic payment systems files here. Get all free photos.
If you’re searching for money laundering techniques with electronic payment systems images information related to the money laundering techniques with electronic payment systems keyword, you have visit the right blog. Our site always gives you suggestions for viewing the maximum quality video and picture content, please kindly surf and locate more enlightening video content and graphics that fit your interests.
Money Laundering Techniques With Electronic Payment Systems. Enfield Publishing Distribution Company. The placement stage involves the phys-. This technique involves the use of many individuals thesmurfs who exchange illicit funds in smaller less conspicuous amounts for highly liquid items such as traveller cheques bank drafts or deposited directly into savings accounts. Prosecutors called it possibly the biggest money-laundering case in US history.
 Pdf Money Laundering Techniques With Electronic Payment Systems Semantic Scholar From semanticscholar.org
Pdf Money Laundering Techniques With Electronic Payment Systems Semantic Scholar From semanticscholar.org
In todays environment money laundering is generally undertaken through four primary methods. After the 2006 New Payment Method NPM report the growing use of NPMs and an increased awareness of associated money laundering and terrorist financing risks have resulted in the detection of a number of money laundering cases over the last four years. Methods such as micro laundering where thousands of small electronic payments are made through platforms such as PayPal to avoid triggering alerts are increasingly common and more difficult to detect. The money laundering techniques involve direct use of electronic payment systems for terrorism financing or their use only as a transporting instrument in one of the three phases of the money laundering cycle. The use of the Internet allows money launderers to easily avoid detection. This technique involves the use of many individuals thesmurfs who exchange illicit funds in smaller less conspicuous amounts for highly liquid items such as traveller cheques bank drafts or deposited directly into savings accounts.
Breaking down large sums of money into smaller amounts that can be deposited in banks without triggering AML reporting threshold alerts.
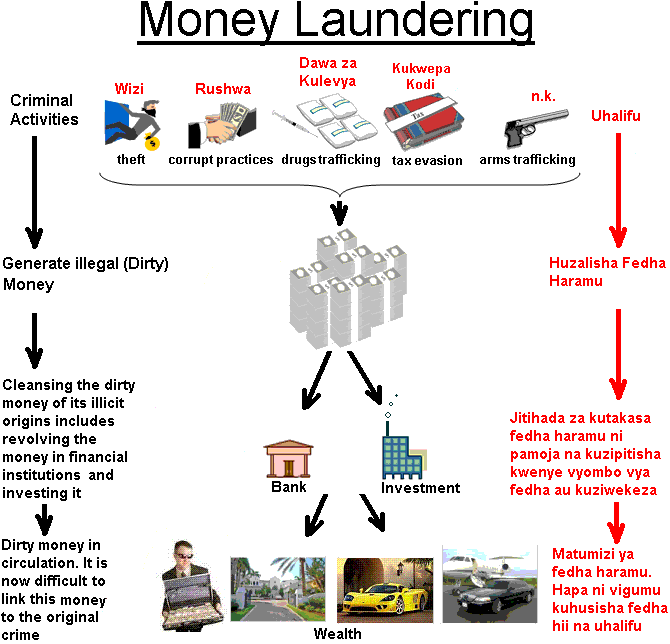
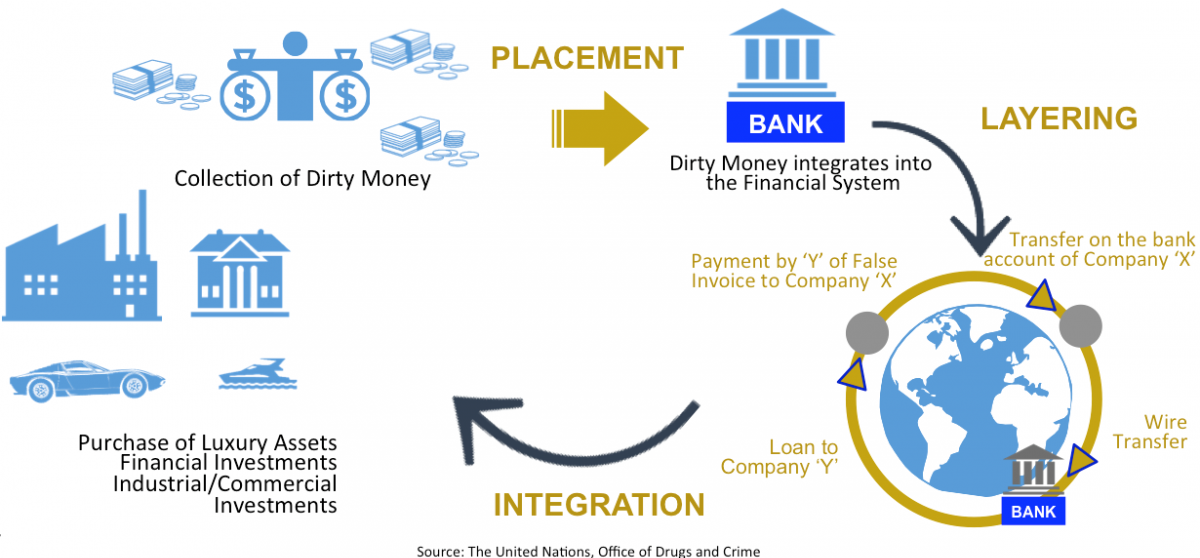
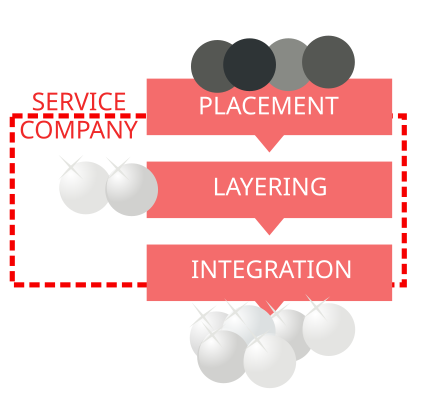
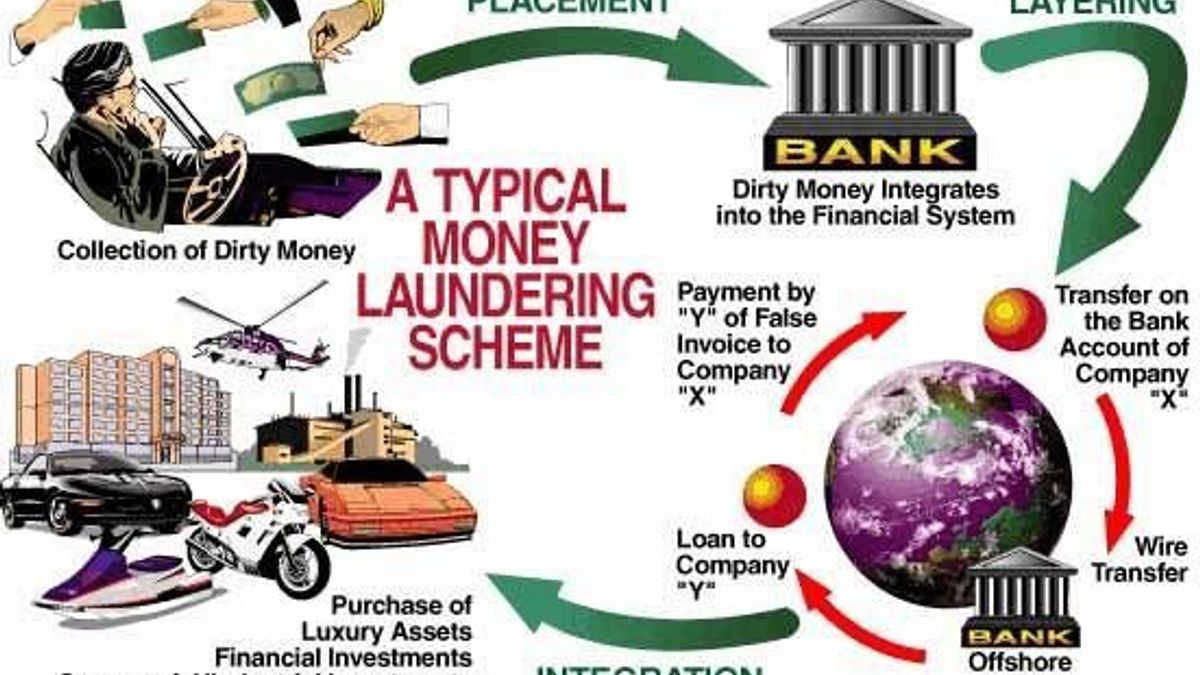
Evolution of Money Laundering Techniques. Money laundering was primarily related to terrorism and illegal sales of arms rather than drug trafficking. Lets take a look at a recent money laundering case that involved virtual currencies. Integration is the third stage of the money laundering process in which the illegal funds or assets are successfully cleansed and appear legitimate in the financial system making them available for investment saving or expenditure. Electronic cash transfers occur on an existing infrastructure - the Internet - and through existing. Stages Involved in Typical Money Laundering Scheme Exhibit 2.
![]() Source: zerotheft.net
Source: zerotheft.net
Evolution of Money Laundering Techniques. After the 2006 New Payment Method NPM report the growing use of NPMs and an increased awareness of associated money laundering and terrorist financing risks have resulted in the detection of a number of money laundering cases over the last four years. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in. Operating this conventional money exchange system is expensive. Another common technique is to use online transactions via sites such as eBay to facilitate the laundering.
 Source: present5.com
Source: present5.com
Download Citation On Jan 1 2006 Krzysztof Woda published Money Laundering Techniques with Electronic Payment Systems Find read and cite all the research you need on. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in. The first stage in the process is placement. Enfield Publishing Distribution Company. Funneling illegal funds through legitimate businesses that deal heavily in cash transactions.
 Source: tookitaki.ai
Source: tookitaki.ai
Another common technique is to use online transactions via sites such as eBay to facilitate the laundering. Stages Involved in Typical Money Laundering Scheme Exhibit 2. Federal law enforcement charged Liberty Reserve a digital currency provider with running a 6 billion digital money-laundering scheme. Trade-based Money Laundering Trade-based money laundering TBML is another alternative remittance system providing a method by which criminal organizations obtain transfer and store criminal proceeds disguised as legitimate trade. In what follows the typical techniques for money laundering involving the use of electronic payment methods and.
Liberty Reserve a centralized digital currency. Evolution of Money Laundering Techniques. Electronic Payment Systems and Money Laundering Risks and Countermeasures in the Post-Internet Hype Era. Trade-based Money Laundering Trade-based money laundering TBML is another alternative remittance system providing a method by which criminal organizations obtain transfer and store criminal proceeds disguised as legitimate trade. It can be furthermore assumed that payment systems differ with regard to their suitability for a single money laundering phase and thereby for terrorist financing.
 Source: gov.si
Source: gov.si
Money laundering was primarily related to terrorism and illegal sales of arms rather than drug trafficking. Federal law enforcement charged Liberty Reserve a digital currency provider with running a 6 billion digital money-laundering scheme. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in. In todays environment money laundering is generally undertaken through four primary methods. Operating this conventional money exchange system is expensive.
 Source: semanticscholar.org
Source: semanticscholar.org
Liberty Reserve a centralized digital currency. Breaking down large sums of money into smaller amounts that can be deposited in banks without triggering AML reporting threshold alerts. Stages Involved in Typical Money Laundering Scheme Exhibit 2. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in. Lets take a look at a recent money laundering case that involved virtual currencies.
 Source: researchgate.net
Source: researchgate.net
The suitability of an electronic payment system for financing of illegal activities depends to a great extent on such supported characteristics as anonymity mobility etc. Operating this conventional money exchange system is expensive. Integration is the third stage of the money laundering process in which the illegal funds or assets are successfully cleansed and appear legitimate in the financial system making them available for investment saving or expenditure. Trade-based Money Laundering Trade-based money laundering TBML is another alternative remittance system providing a method by which criminal organizations obtain transfer and store criminal proceeds disguised as legitimate trade. The project team analysed 33 case studies which mainly involved prepaid cards or internet.
 Source: semanticscholar.org
Source: semanticscholar.org
After the 2006 New Payment Method NPM report the growing use of NPMs and an increased awareness of associated money laundering and terrorist financing risks have resulted in the detection of a number of money laundering cases over the last four years. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in. The money laundering techniques involve direct use of electronic payment systems for terrorism financing or their use only as a transporting instrument in one of the three phases of the money laundering cycle. Liberty Reserve a centralized digital currency. In what follows the typical techniques for money laundering involving the use of electronic payment methods and.
 Source: wikiwand.com
Source: wikiwand.com
Criminals may use several methodologies to place illegal money in the legitimate financial system including. Electronic cash transfers occur on an existing infrastructure - the Internet - and through existing. This technique involves the use of many individuals thesmurfs who exchange illicit funds in smaller less conspicuous amounts for highly liquid items such as traveller cheques bank drafts or deposited directly into savings accounts. Electronic Payment Systems and Money Laundering Risks and Countermeasures in the Post-Internet Hype Era. After the 2006 New Payment Method NPM report the growing use of NPMs and an increased awareness of associated money laundering and terrorist financing risks have resulted in the detection of a number of money laundering cases over the last four years.
 Source: researchgate.net
Source: researchgate.net
After the 2006 New Payment Method NPM report the growing use of NPMs and an increased awareness of associated money laundering and terrorist financing risks have resulted in the detection of a number of money laundering cases over the last four years. Stages Involved in Typical Money Laundering Scheme Exhibit 2. Money laundering was primarily related to terrorism and illegal sales of arms rather than drug trafficking. Download Citation On Jan 1 2006 Krzysztof Woda published Money Laundering Techniques with Electronic Payment Systems Find read and cite all the research you need on. The project team analysed 33 case studies which mainly involved prepaid cards or internet.
 Source: integrity-asia.com
Source: integrity-asia.com
Electronic cash transfers occur on an existing infrastructure - the Internet - and through existing. In what follows the typical techniques for money laundering involving the use of electronic payment methods and. Electronic cash transfers occur on an existing infrastructure - the Internet - and through existing. Another common technique is to use online transactions via sites such as eBay to facilitate the laundering. The money laundering techniques involve direct use of electronic payment systems for terrorism financing or their use only as a transporting instrument in one of the three phases of the money laundering cycle.
 Source: researchgate.net
Source: researchgate.net
Lets take a look at a recent money laundering case that involved virtual currencies. Electronic Payment Systems and Money Laundering Risks and Countermeasures in the Post-Internet Hype Era. Another common technique is to use online transactions via sites such as eBay to facilitate the laundering. The placement stage involves the phys-. The agency funded several projects to explore the feasibility of using artificial intelligence techniques to detect electronic money laundering but when its budget was tightened in.
 Source: jagranjosh.com
Source: jagranjosh.com
The money laundering techniques involve direct use of electronic payment systems for terrorism financing or their use only as a transporting instrument in one of the three phases of the money laundering cycle. The rise of online banking institutions anonymous online payment services peer-to. Money laundering was primarily related to terrorism and illegal sales of arms rather than drug trafficking. The use of the Internet allows money launderers to easily avoid detection. Operating this conventional money exchange system is expensive.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title money laundering techniques with electronic payment systems by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.