13+ Money laundering techniques to avoid detection info
Home » money laundering Info » 13+ Money laundering techniques to avoid detection infoYour Money laundering techniques to avoid detection images are ready. Money laundering techniques to avoid detection are a topic that is being searched for and liked by netizens today. You can Find and Download the Money laundering techniques to avoid detection files here. Find and Download all royalty-free photos and vectors.
If you’re searching for money laundering techniques to avoid detection pictures information related to the money laundering techniques to avoid detection interest, you have pay a visit to the right site. Our site always gives you hints for viewing the maximum quality video and image content, please kindly hunt and locate more informative video content and graphics that match your interests.
Money Laundering Techniques To Avoid Detection. This is a policy where deposits must stay in an account for a minimum of five trading days. Stage 1 of Money Laundering. Another tactic to help prevent money laundering is the AML holding period. Consequently detecting money laundering requires an the discretion of.
 5 Methods That Modern Money Launderers Use To Beat Detection Tookitaki Tookitaki From tookitaki.ai
5 Methods That Modern Money Launderers Use To Beat Detection Tookitaki Tookitaki From tookitaki.ai
Additionally true value is often difficult to set accurately. Detection logic focused on simple transactional behavior will never successfully identify money laundering operations by sophisticated hybrid threats like Hezbollah. It is important for us to understand the origin of the source of funds by having a swift reliable identification verification system to stop offenders in the beginning stages of money laundering. The use of the Internet allows money launderers to easily avoid detection. Here are five ways to be proactive and vigilant in your fight against money launderers. Recognize ML patterns by different techniques such as.
Others involve computer graphics and.
Recognize ML patterns by different techniques such as. To make the dirty money appear to be clean deposits are made into domestic banks by splitting the large amount into smaller amounts and making multiple deposits below reporting limits to avoid detection. Abstract Money laundering laundering and evolves using multiple layers of trade multi trading methods and uses multiple components in order to evade detection and prevention techniques. Text analyticstext mining this involves the use of natural language processing and statistical and machine learning techniques to model and structure information from. For money laundering purposes a criminal may transfer money directly to such victims account and trick the person into sharing sensitive information such as passwords or into getting remote access to the victims computer. Over-and under-invoicing of the goods and services.
 Source: fineksus.com
Source: fineksus.com
Slowing down the process assists with anti-money laundering measures and allows more time for risk assessments to take place. Key issues in anti-money laundering AML are. Money laundering detection techniques. Anti-money laundering using machine learning techniques are able to identify suspicious transactions and also irregular networks of transactions. Ask a Lot of Questions.
 Source: pideeco.be
Source: pideeco.be
For money laundering purposes a criminal may transfer money directly to such victims account and trick the person into sharing sensitive information such as passwords or into getting remote access to the victims computer. Abstract Money laundering laundering and evolves using multiple layers of trade multi trading methods and uses multiple components in order to evade detection and prevention techniques. Another tactic to help prevent money laundering is the AML holding period. First ask about the amount of money. These transactions are flagged for investigation and can be scored as high medium or low priority so that the investigator is.
 Source: amlbot.com
Source: amlbot.com
Identifying the modus operandi identifying monetary instruments and institutions involved identifying parties and beneficiaries involved proving. Key issues in anti-money laundering AML are. The most commonly used trade-based money laundering techniques are. They aim to provide. Support vector machine 4 correlation analysis 5 hi stogram analysis 5 etc.
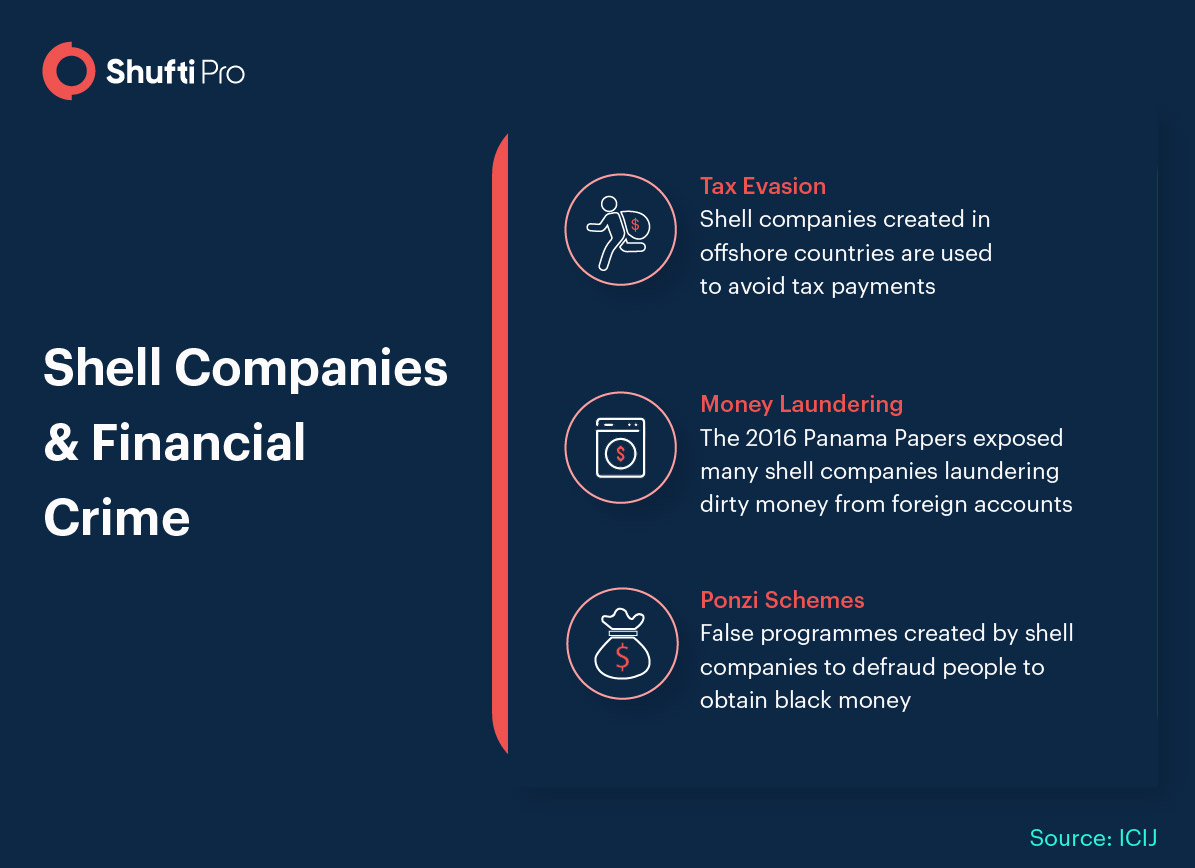 Source: shuftipro.com
Source: shuftipro.com
This is a policy where deposits must stay in an account for a minimum of five trading days. Ask a Lot of Questions. To make the dirty money appear to be clean deposits are made into domestic banks by splitting the large amount into smaller amounts and making multiple deposits below reporting limits to avoid detection. This is a policy where deposits must stay in an account for a minimum of five trading days. Techniques such as under- or over-invoicing falsifying documents and misrepresenting financial transactions are difficult to trace as they can involve multiple parties jurisdictions and transactions.
 Source: datavisor.com
Source: datavisor.com
Detecting Money Laundering t the core of all wire transfer monitoring proposals are one or. Over-and under-invoicing of the goods and services. Money laundering is getting harder to detect and trace due to the changing technology and integration of economies among markets. Consequently detecting money laundering requires an the discretion of. Here are five ways to be proactive and vigilant in your fight against money launderers.
 Source: co.pinterest.com
Source: co.pinterest.com
The most commonly used trade-based money laundering techniques are. Techniques such as under- or over-invoicing falsifying documents and misrepresenting financial transactions are difficult to trace as they can involve multiple parties jurisdictions and transactions. Text analyticstext mining this involves the use of natural language processing and statistical and machine learning techniques to model and structure information from. Over-and under-invoicing of the goods and services. A Over-and under-invoicing of the goods and services This is the oldest and most commonly preferred method of money laundering via trade.
 Source: allbankingalerts.com
Source: allbankingalerts.com
Ask a Lot of Questions. Detecting Money Laundering t the core of all wire transfer monitoring proposals are one or more computer technologies. These transactions are flagged for investigation and can be scored as high medium or low priority so that the investigator is. Most of these approaches try to. Techniques such as under- or over-invoicing falsifying documents and misrepresenting financial transactions are difficult to trace as they can involve multiple parties jurisdictions and transactions.
 Source: amlbot.com
Source: amlbot.com
Recognize ML patterns by different techniques such as. When approached with a business proposition there are a number of things you need to ask to ensure that it is a legitimate partnership or if it sends off alerts to potential money laundering. Consequently detecting money laundering requires an the discretion of. Text analyticstext mining this involves the use of natural language processing and statistical and machine learning techniques to model and structure information from. Slowing down the process assists with anti-money laundering measures and allows more time for risk assessments to take place.
 Source: tookitaki.ai
Source: tookitaki.ai
The rise of online banking institutions anonymous online payment. A Over-and under-invoicing of the goods and services This is the oldest and most commonly preferred method of money laundering via trade. Abstract Money laundering laundering and evolves using multiple layers of trade multi trading methods and uses multiple components in order to evade detection and prevention techniques. First ask about the amount of money. Money laundering detection techniques.

Most of these approaches try to. Recognize ML patterns by different techniques such as. This method is used to avoid detection and anti-money laundering. Although the specific techniques used to clean dirty money vary financial experts cite three stages of money laundering in the process. Slowing down the process assists with anti-money laundering measures and allows more time for risk assessments to take place.
 Source: planetcompliance.com
Source: planetcompliance.com
Although the specific techniques used to clean dirty money vary financial experts cite three stages of money laundering in the process. Money laundering is getting harder to detect and trace due to the changing technology and integration of economies among markets. Text analyticstext mining this involves the use of natural language processing and statistical and machine learning techniques to model and structure information from. Money laundering detection techniques. Support vector machine 4 correlation analysis 5 hi stogram analysis 5 etc.
 Source: regtechtimes.com
Source: regtechtimes.com
Identifying the modus operandi identifying monetary instruments and institutions involved identifying parties and beneficiaries involved proving. Money laundering is getting harder to detect and trace due to the changing technology and integration of economies among markets. Most of these approaches try to. Others involve computer graphics and. Money laundering detection techniques.
 Source: amlbot.com
Source: amlbot.com
The use of the Internet allows money launderers to easily avoid detection. The use of the Internet allows money launderers to easily avoid detection. Money laundering is getting harder to detect and trace due to the changing technology and integration of economies among markets. Recognize ML patterns by different techniques such as. Additionally true value is often difficult to set accurately.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title money laundering techniques to avoid detection by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.