18+ Money laundering detection methods ideas
Home » money laundering Info » 18+ Money laundering detection methods ideasYour Money laundering detection methods images are ready. Money laundering detection methods are a topic that is being searched for and liked by netizens today. You can Get the Money laundering detection methods files here. Get all free photos.
If you’re looking for money laundering detection methods pictures information connected with to the money laundering detection methods interest, you have pay a visit to the ideal blog. Our site always provides you with hints for viewing the maximum quality video and picture content, please kindly surf and find more informative video content and images that fit your interests.
Money Laundering Detection Methods. The most commonly used trade-based money laundering techniques are. Layering The purpose of. Current countermea-sures taken by nancial organizations are based onlegal requirements and very basic statistical analy-sis. For 1 the methods try to identify patterns in the data without information on which data correspond to money laundering and not.
 Pdf Data Mining Techniques For Anti Money Laundering Semantic Scholar From semanticscholar.org
Pdf Data Mining Techniques For Anti Money Laundering Semantic Scholar From semanticscholar.org
What are the different techniques to detect money laundering. From reference 1 we can see that anti-money laundering issue is much more obvious and needs. However labels are so scarce that traditional supervised algorithms are inapplicable. This method is used to avoid detection and anti-money laundering. The major purpose is to change the form of the proceeds from conspicuous bulk cash to some equally valuable but less conspicuous form. Money laundering detection started in the 1970 s with financial institutions reporting transactions to the government Soltani Nguyen Yang Faghani Yagoub An 2016.
Money Laundering Detection System Money Laundering Detection System MLDS is part module of the system supporting work of the police analyst CASTLINK which is being developed at the AGH University of Science and Technology in cooperation with the Polish State Police.
Historically methods of money laundering have included smurfing or the structuring of the banking of large amounts of money into multiple small transactions often. Money laundering detection started in the 1970 s with financial institutions reporting transactions to the government Soltani Nguyen Yang Faghani Yagoub An 2016. Some researches have been carried on but the problem is not thoroughly solved. However labels are so scarce that traditional supervised algorithms are inapplicable. For 1 the methods try to identify patterns in the data without information on which data correspond to money laundering and not. Current countermea-sures taken by nancial organizations are based onlegal requirements and very basic statistical analy-sis.
 Source: bobsguide.com
Source: bobsguide.com
Others involve computer graphics and statistical computing. According to the Global Financial Integrity analysis from 2005-2014 the illicit cash flow to and from emerging and developing countries was 12-24 of their total trade. Cryptocurrencies in particular have developed as a haven for money laundering activity. The MoneyLaundering Process When money is obtained from various illegal activities such as corruption bribery tax evasion drugs where the criminal does not want the authorities to know the source of the income they engage in money laundering. Machine Learning can be used to detect these illicit patterns.
 Source: semanticscholar.org
Source: semanticscholar.org
However labels are so scarce that traditional supervised algorithms are inapplicable. Current countermea-sures taken by nancial organizations are based onlegal requirements and very basic statistical analy-sis. Some researches have been carried on but the problem is not thoroughly solved. Here we address money laundering detection assuming minimal access to labels. The major purpose is to change the form of the proceeds from conspicuous bulk cash to some equally valuable but less conspicuous form.
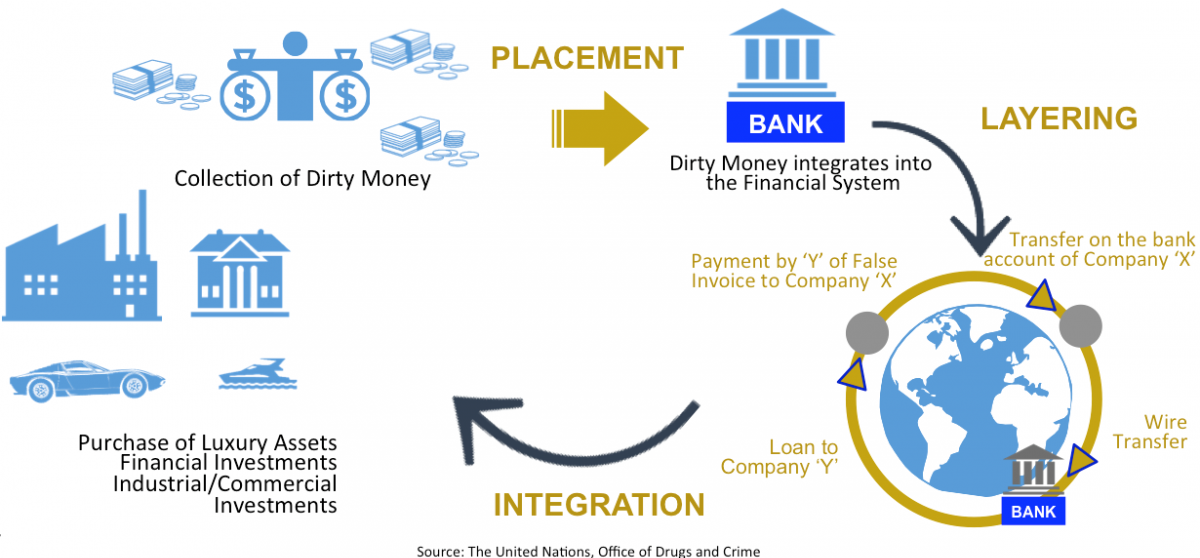 Source: gov.si
Source: gov.si
By misinterpreting the price of the goods or the services an extra value can be transferred between the parties of the trade. Identifying the modus operandi identifying monetary instruments and institutions involved identifying parties and beneficiaries involved proving. The major purpose is to change the form of the proceeds from conspicuous bulk cash to some equally valuable but less conspicuous form. Here we address money laundering detection assuming minimal access to labels. By misinterpreting the price of the goods or the services an extra value can be transferred between the parties of the trade.
 Source: researchgate.net
Source: researchgate.net
By misinterpreting the price of the goods or the services an extra value can be transferred between the parties of the trade. The most commonly used trade-based money laundering techniques are. Layering The purpose of. Money laundering detection started in the 1970 s with financial institutions reporting transactions to the government Soltani Nguyen Yang Faghani Yagoub An 2016. Key issues in anti-money laundering AML are.
 Source: semanticscholar.org
Source: semanticscholar.org
These methods canbe based on supervised and unsupervised. Historically methods of money laundering have included smurfing or the structuring of the banking of large amounts of money into multiple small transactions often. However labels are so scarce that traditional supervised algorithms are inapplicable. Money laundering ML is a major issue for the Department of Homeland Security DHS and US Treasury. What are the different techniques to detect money laundering.
 Source: semanticscholar.org
Source: semanticscholar.org
Criminals use money laundering to make the pro-ceeds from their illegal activities look legitimate inthe eyes of the rest of society. Since then most of the techniques used in automated banking systems have established rules with certain thresholds. Money laundering detection started in the 1970 s with financial institutions reporting transactions to the government Soltani Nguyen Yang Faghani Yagoub An 2016. Money laundering detection techniques. For 2 latter the methods attempt to learn the patterns that differentiate between money laundering and legitimate operations by using data where the labeloutcome money laundering or not is known.
 Source: researchgate.net
Source: researchgate.net
Criminals use money laundering to make the pro-ceeds from their illegal activities look legitimate inthe eyes of the rest of society. Others involve computer graphics and statistical computing. From reference 1 we can see that anti-money laundering issue is much more obvious and needs. What are the different techniques to detect money laundering. Cryptocurrencies in particular have developed as a haven for money laundering activity.
 Source: researchgate.net
Source: researchgate.net
Here we address money laundering detection assuming minimal access to labels. For 1 the methods try to identify patterns in the data without information on which data correspond to money laundering and not. Money laundering detection started in the 1970 s with financial institutions reporting transactions to the government Soltani Nguyen Yang Faghani Yagoub An 2016. The MoneyLaundering Process When money is obtained from various illegal activities such as corruption bribery tax evasion drugs where the criminal does not want the authorities to know the source of the income they engage in money laundering. They dynamically evolve expand and contract over fraudster networks in different countries.
 Source: sciencedirect.com
Source: sciencedirect.com
From reference 1 we can see that anti-money laundering issue is much more obvious and needs. However labels are so scarce that traditional supervised algorithms are inapplicable. Identifying the modus operandi identifying monetary instruments and institutions involved identifying parties and beneficiaries involved proving. Detecting Money Laundering t the core of all wire transfer monitoring proposals are one or more computer technologies. These methods canbe based on supervised and unsupervised.
 Source: moneylaunderingnews.com
Source: moneylaunderingnews.com
Many of these technologies rely upon techniques developed in the field of artificial intelligence AI. They dynamically evolve expand and contract over fraudster networks in different countries. The major purpose is to change the form of the proceeds from conspicuous bulk cash to some equally valuable but less conspicuous form. Cryptocurrencies in particular have developed as a haven for money laundering activity. Machine Learning can be used to detect these illicit patterns.
 Source: researchgate.net
Source: researchgate.net
RELATED WORK Money laundering is a serious crime which makes it necessary to develop detection methods in transactions. However labels are so scarce that traditional supervised algorithms are inapplicable. Money laundering ML is a major issue for the Department of Homeland Security DHS and US Treasury. Criminals use money laundering to make the pro-ceeds from their illegal activities look legitimate inthe eyes of the rest of society. Machine Learning oers a number of ways todetect anomalous transactions.
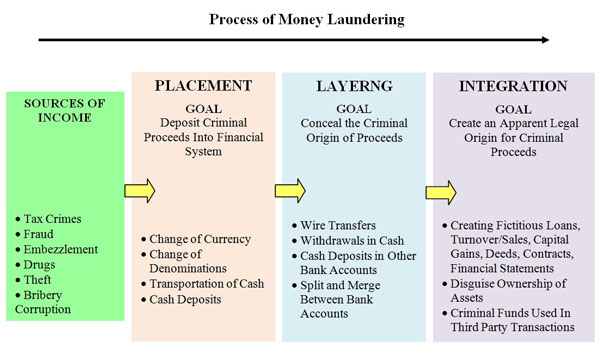 Source: calert.info
Source: calert.info
Current countermea-sures taken by nancial organizations are based onlegal requirements and very basic statistical analy-sis. These methods canbe based on supervised and unsupervised. Money laundering detection techniques. The major purpose is to change the form of the proceeds from conspicuous bulk cash to some equally valuable but less conspicuous form. Current countermea-sures taken by nancial organizations are based onlegal requirements and very basic statistical analy-sis.
 Source: tookitaki.ai
Source: tookitaki.ai
Detecting Money Laundering t the core of all wire transfer monitoring proposals are one or more computer technologies. According to the Global Financial Integrity analysis from 2005-2014 the illicit cash flow to and from emerging and developing countries was 12-24 of their total trade. Here we address money laundering detection assuming minimal access to labels. Others involve computer graphics and statistical computing. Money laundering ML is a major issue for the Department of Homeland Security DHS and US Treasury.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title money laundering detection methods by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.